Booking.com 2.0: More Scams from the #1 Travel Site
Last week, we covered the recent breach of Booking.com—an event that has impacted hoteliers by compromising sensitive information of many travelers.
This week, we’ve got an update on this issue and are highlighting another Booking.com related threat: targeted attacks on partner hotel networks to enable sophisticated, highly realistic phishing scams.
If this sounds complex—the presence of multiple, independent threats surrounding a single vector like travel sites—well, that’s fair. The evolving and multifaceted nature of threats surrounding Booking.com is yet another example of the inherently complicated landscape of cybersecurity.
Let’s clear that up by diving in.
Partner Breaches
Scammers have long targeted Booking.com customers, a class of hospitality-centric consumers with profiles that are rich in personally identifiable information (PII).
In the latest scam, they are attempting to do so by accessing the Booking.com backend to gain information about guests, their personal information, and their upcoming stays. Once in the backend, criminals can then craft highly personalized phishing emails or send messages to guests directly to the platform.
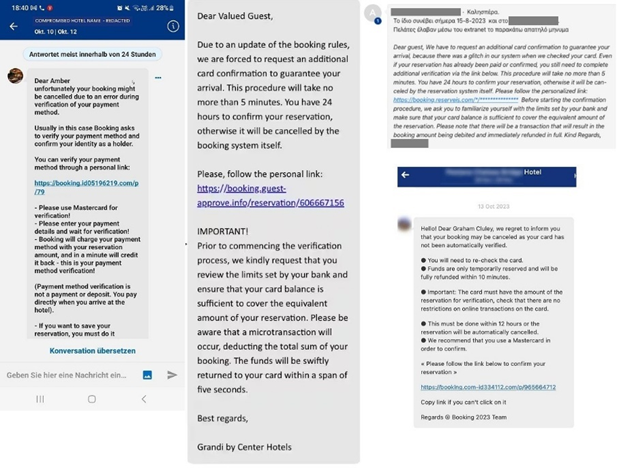
Scam attempts from Booking.com’s internal messaging system. (Source: Kaspersky)
How do scammers get access to the Booking.com backend? By stealing the credentials of hoteliers.
Check out this reported scenario, featured in The Economic Times:
“[T]he threat actor initiated contact by emailing a member of the hotel’s operations staff.
The sender claimed to be a former guest who had lost an identification document (ID), and they requested the recipient’s assistance in finding it. The email did not include an attachment or malicious links, and it was likely intended to gain the recipient’s trust.
With no reason to be suspicious, the employee responded to the email and requested additional information.
Later, the threat actor sent another email about the lost ID. The sender identified the document as a passport and stated that they strongly believed they left it at the hotel.
When the recipient clicked the link in the email, a ZIP archive file was downloaded to the computer’s desktop.”
What To Do
In many ways, the best response to this threat is to maintain the habits of any secure organisation—engage in training, ongoing awareness efforts, and ensure that your company enforces policies that define best practices of data protection. And, of course, share informational piece such as this article to make your team cognizant of the threat and able to spot it.
In addition, though, there are a few specific recommendations provided by IT professionals. From Kaspersky:
“*Storing passwords in your browser is not safe — that’s where stealer malware always looks for them. To store passwords well, use a specialized application — a password manager — that will take care of their security.
*It’s essential to install reliable protection on all your devices used for business.
*Take particular care of the security of those computers that employees might use to communicate with strangers — they’re the ones more likely to become the target of an attack.“
Feeling overwhelmed? Don’t be. VENZA is here to help. Cybersecurity is complex, but in partnership with us, your company can get started in as little as one month. Get a live demonstration today by contacting our Customer Success Team.
Ready to elevate your game? Contact Sales to discuss signing up for our programs or adding new solutions to your contract.
***
Take VENZA’s free Phishing Test to assess gaps in your human firewall today!

Training your personnel to recognize and report phishing attempts is essential to protecting your guests and their data. Get started by determining your risk and readiness level using this free tool.
***
Want to stay informed? Subscribe to the free VENZA Echo now. You’ll receive a monthly digest with the highlights of our weekly article series and important product updates and news from VENZA.
